Azure Private Link is a new service on Azure that helps you secure your PaaS services.
Normally, if you connect to a SQL Azure database, a storage account or a Web App, the traffic is routed over the public internet which could be a security issue. You can configure your service to whitelist certain IP addresses or require users to be signed in before they can access your resource but wouldn’t it be nicer if your PaaS resource wasn’t accessible over the public internet?
That’s what Azure Private Link offers and in this blog post I want to share my first experiences with this new service.
Using Private Link to secure a SQL Azure database
One of the services that supports Private Link is SQL Azure. Azure SQL Server can be reached through an address such as https://my-database.database.windows.net. When you configure a Private Endpoint connection for your SQL Server, you map a private IP Address in your virtual network to your SQL Server instance.
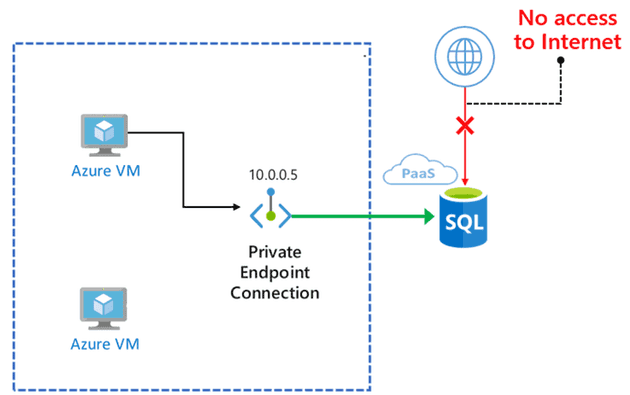
The following picture shows an overview of the resources I created. I have two Virtual Machines. The first one (VM A) is linked to a virtual network that has a Private Endpoint that points to IP address 10.0.0.5. That IP address is mapped to your SQL Server. Internet access for SQL Server is disabled. The second VM (VM B) is not inside the vNet and cannot access your SQL Server.
I’ve build this scenario by following https://docs.microsoft.com/en-us/azure/private-link/create-private-endpoint-portal and adding an additional Virtual Machine.
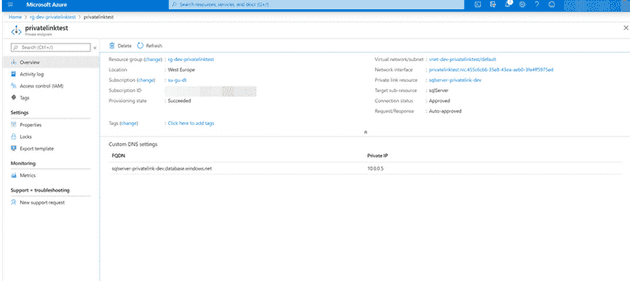
The most important element is the Private Endpoint that maps a FQDN to a local IP address in the subnet:
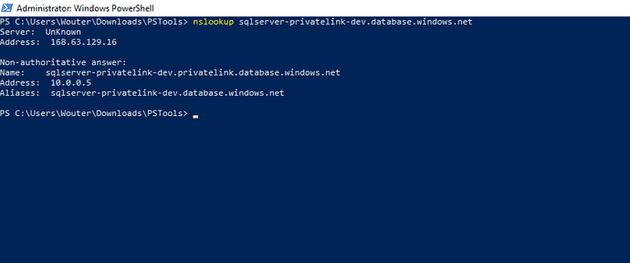
When I run nslookup on VM A I get the following result:
As you an see, the public FQDN sqlserver-privatelink-dev.database.windows.net is mapped to ip address 10.0.0.5.
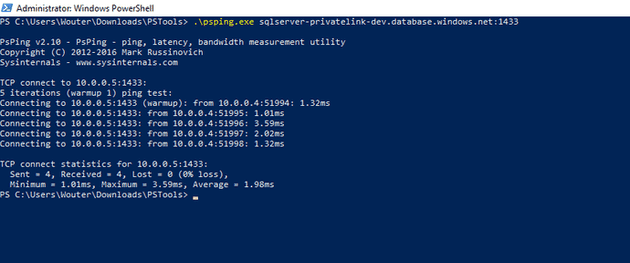
When I run psping I get the following:
As you can see, connections to my SQL Server on port 1433 are translated as a connection to 10.0.0.5.
I’ve now got a local IP address in my vNet that is used to access a PaaS service.
Disabling public access
I was a bit surprised that when I used SQL Server Management studio on VM B to connect to my SQL Server, I got a prompt if I wanted to whitelist my IP address in the SQL Server firewall.
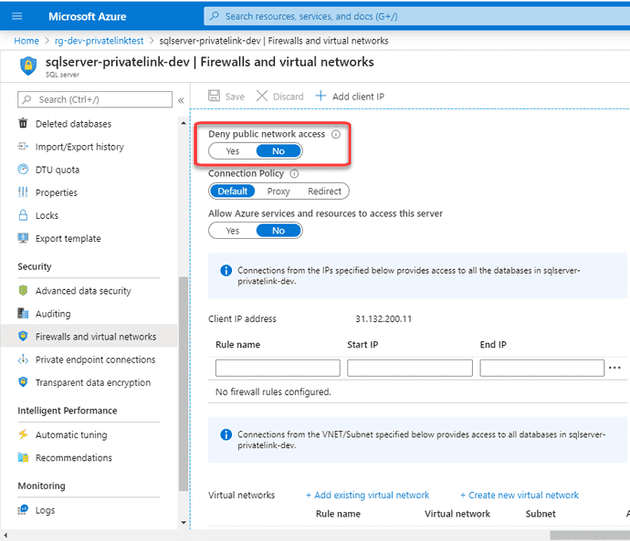
When looking at the settings of my SQL Server I forgot to enable the following property:
After denying all public access, I can no longer connect from VM B to my SQL Server.
Conclusion
Private Link is something that a lot of my customers have been waiting for. This way, you can easily restrict access to resources and configure access as a part of your local vNet. More and more services support Azure Private Link and it’s definitely a feature to start implementing in your Azure environments.
Questions? Comments? Please reach out!